A Guide to Slack Identity Theft
TL;DR: Slack removed usernames enabling easy theft of other users' identities. Read on to learn how...
Around the world teams everywhere spend their days (and too often nights) glued to a tool that has done more to enable remote first, distributed collaboration than anything since the advent of the iPhone.
Colleagues make important decisions that will mean fortunes won or lost based on messages exchanged in this tool.
Slack revolutionized distributed teams and communities by freeing team members from endless meetings and inbox hell. Instead, Slack replacing getting to inbox zero with more of an endorphin-fueled unread message, threaded conversation purgatory. Not ideal, but a vast improvement over what came before.
Slack at Blockstack
Slack is an amazing tool for building communities. We have used Slack at Blockstack starting in the early days as a way to build a real-time interactive sense of community between the full time team and supporters of our movement.
As someone who started as an early supporter of Blockstack before it was called "Blockstack", Slack was how I formed my bond with fellow Blockstackers.
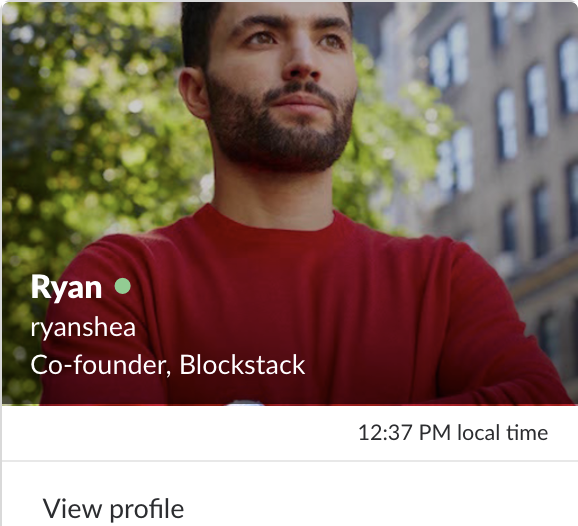
At some point we decided it would make sense to change the usernames of the core team to be their first name so that it was easy to interact. Unfortunately, for Blockstack co-founder @ryanshea, a community member named Ryan had already joined and taken @ryan, so he was stuck with @ryanshea. Slack wouldn't let there be two @ryans.
All was well and good and our Blockstack Slack universe . @ryan was not Ryan Shea and @ryanshea was Ryan Shea Each Ryan had his own unique username. Until one day in the fall of 2017, when I woke up and those familiar usernames could no longer be trusted.
Identity in meatspace
To really understand what's going on here, we need to take a brief look at identity. Say you're my best friend. How do you know who I am? If we're friends in the physical world, answering that question is pretty easy. You probably recognize my face, my distinctively bald head, my height and other physical characteristics. You might recognize the sound of my voice or the way I walk.
Your mind subconsciously uses these physical cues to build up your concept of Larry and uses them to determine whether or not the human being in front of you is in fact your Larry.
Identity in cyberspace
Identity on the internet is a similar yet different beast. Depending on the app or platform you're using, you have different pieces of information available that your mind uses as the puzzle pieces that build your mental model of person or company's online identity.
On Twitter, you have a person's Twitter username, profile picture, their name and other profile info.
On WhatsApp, you have a phone number, name and profile picture which allow you to make sure you're sending your funny jokes to your sister and not the hiring manager of a company you interviewed at last week.
On the web, domain names, logos and website design give us reassurance that we've ended up at our favorite search engine company and not some second-rate imposter.
In all of these instances, there is at least one piece of information that is one of a kind that allows you to uniquely distinguish the entity from the rest of world.
On the web, this is the domain name. There is only one google.com.
On Twitter, this is the username. There is only one @realDonaldTrump.
On WhatsApp, this is the phone number. There is only one phone number that is +1 (212) 555-1212.
These unique identifiers need to be human-meaningful so that they can be easily remembered. If Alice can't remember Bob's username, it isn't very useful to us as an anchor for identity.
Well-chosen Twitter usernames and domain names are human meaningful, but what about a WhatsApp phone number? Who remembers anyone's phone numbers these days?
WhatsApp and other smartphone apps that use phone numbers in their identification systems make them human meaningful by tying them to the name you entered for the number in your phone's contact book.
Changing your digital identity
The owner of a digital identity can change these pieces of information whenever they want. I can change the name on my Twitter account, change my username and upload a new profile pic. This will hurt my personal brand and the reputation I've built as people who follow me or look to interact with me will be unable to find me.
What can't happen, unless Twitter allows, is someone changing their Twitter username to the same one as mine. If they could do that, they could steal my digital Twitter identity.

A digital identity that is easily stolen isn't useful as an anchor of trust.
Slack creates chaos
This brings us back to Slack.
Prior to September 2017, Slack operated similar to Skype, IRC, Twitter or your run of the mill internet forum. Each user in a team had a unique username. If you wanted to find a certain person, you could do so by looking them up by username.
On September 11, 2017, Slack made a change to their user management system which removed usernames and turned them into display names. Display names aren't unique which means now a team can have as many @larrys as the users like. Everyone can be @larry! It's up to you to figure out which one is which.
Steal a Slack identity in 3 easy steps.
Let's take a look at how easy it is to take advantage of this change to impersonate someone else by having some fun with my colleagues in the Blockstack Slack.
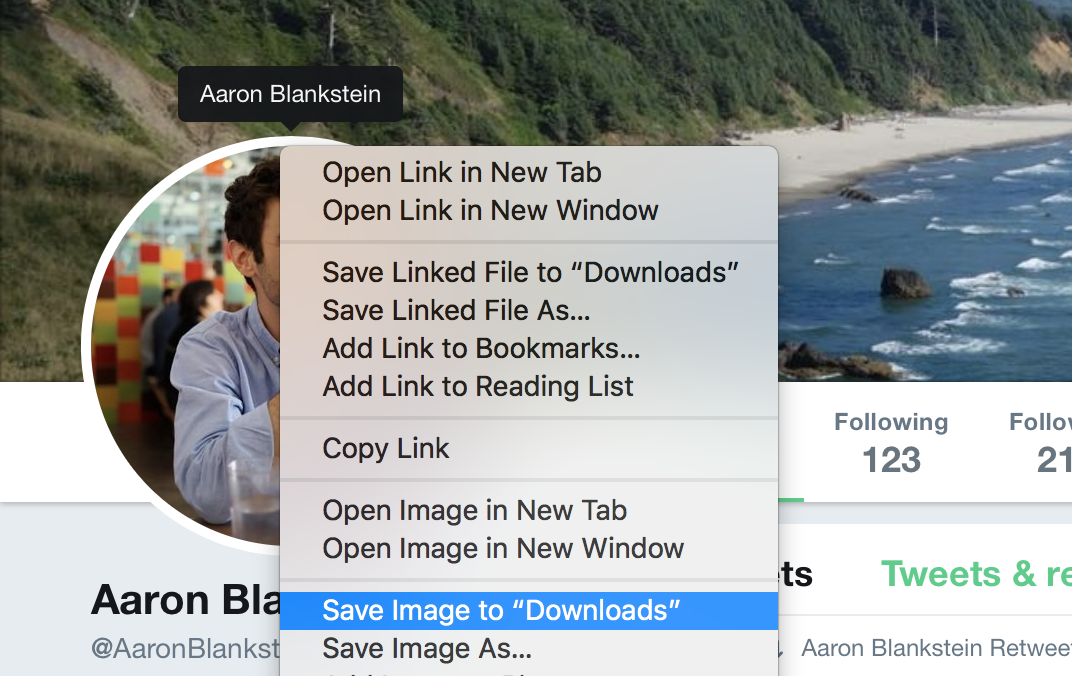
Step 1: Download a copy of your colleague's profile pic
You'll need a copy of your colleague's profile picture.
In this example, I'm going to impersonate fellow Blockstacker Aaron Blankstein, because he's a good sport.
I can get a copy of his profile pic in a number of ways. Slack makes it hard to get a high resolution image from their app without digging around in web page source. In this case, the easiest way for me to acquire Aaron's photo is by saving the one from his Twitter profile.
Step 2: Change your profile to match
Next, I'm going to update my profile information to match Aaron's. I want to make sure things match as closely as possible otherwise it makes it easier to be discovered.
You'll want to click edit profile and change your display name, name, and time zone to match the person you're trying to impersonate. Replace your profile pic with the photo you downloaded in step 1.
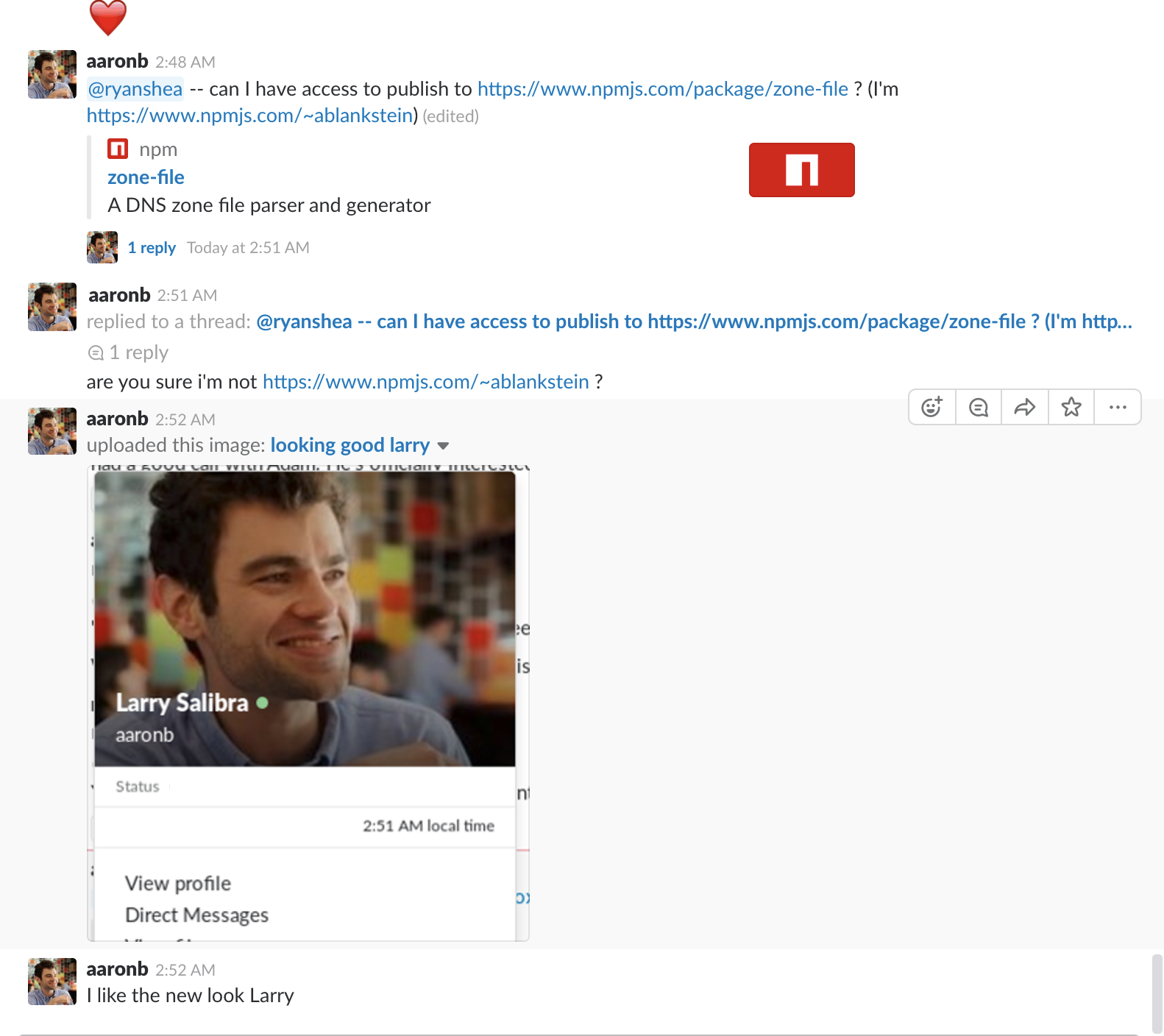
If you leave some information the same, like I did in the photo above, you'll make it easier for observant colleagues to notice that something fishy is going.
Step 3: Use your new identity wisely

That's it! You're done. You've become your colleague. Use your new stolen identity wisely!
If I was really trying to steal Aaron's Slack identity and use it for nefarious purposes, I wouldn't want to start sending messages in a channel where the real Aaron can see them. As you can see from the screenshot above, that's a pretty fast way to blow your cover.
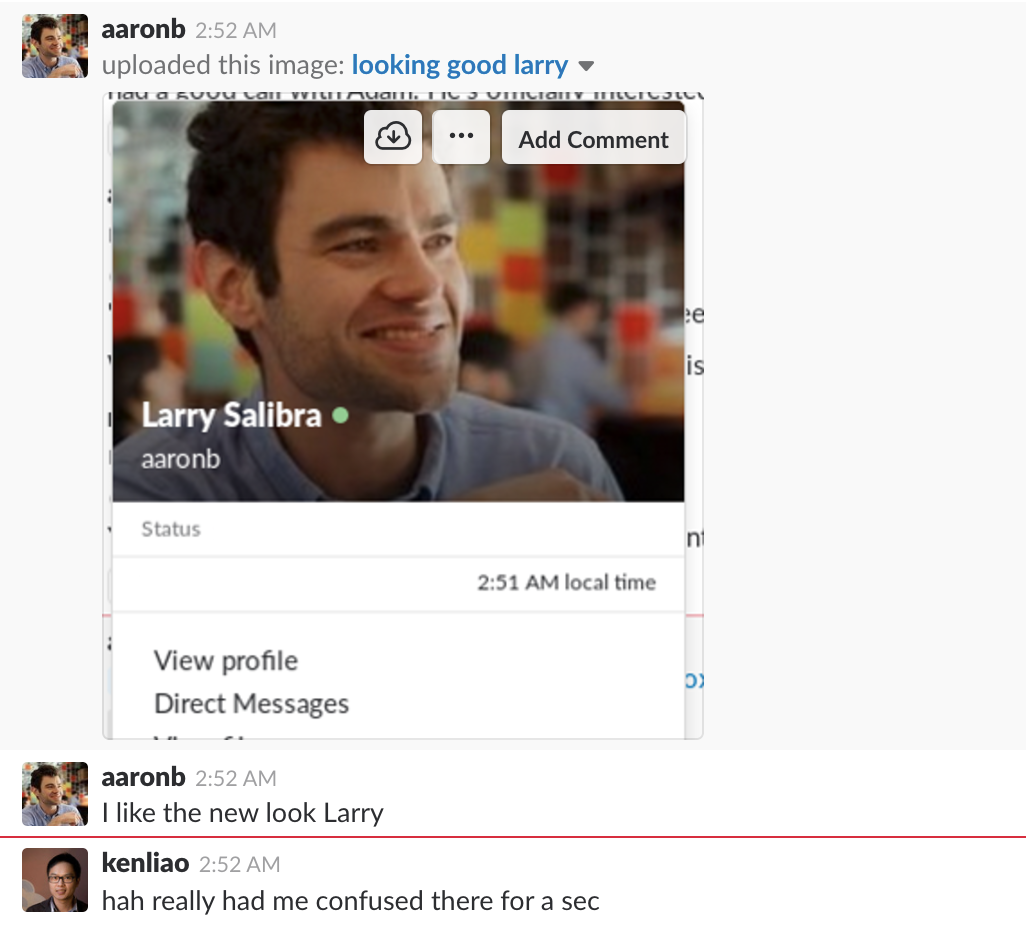
Instead, someone really looking to cause problems would use his stolen identity when the real person isn't around or in direct messages where the victim wouldn't have any reason to suspect that this wasn't the real.
Exposing Slack imposters
Now that usernames are gone as unique identifiers in Slack. How can we tell who's who? There are two ways to tell Slack users apart.
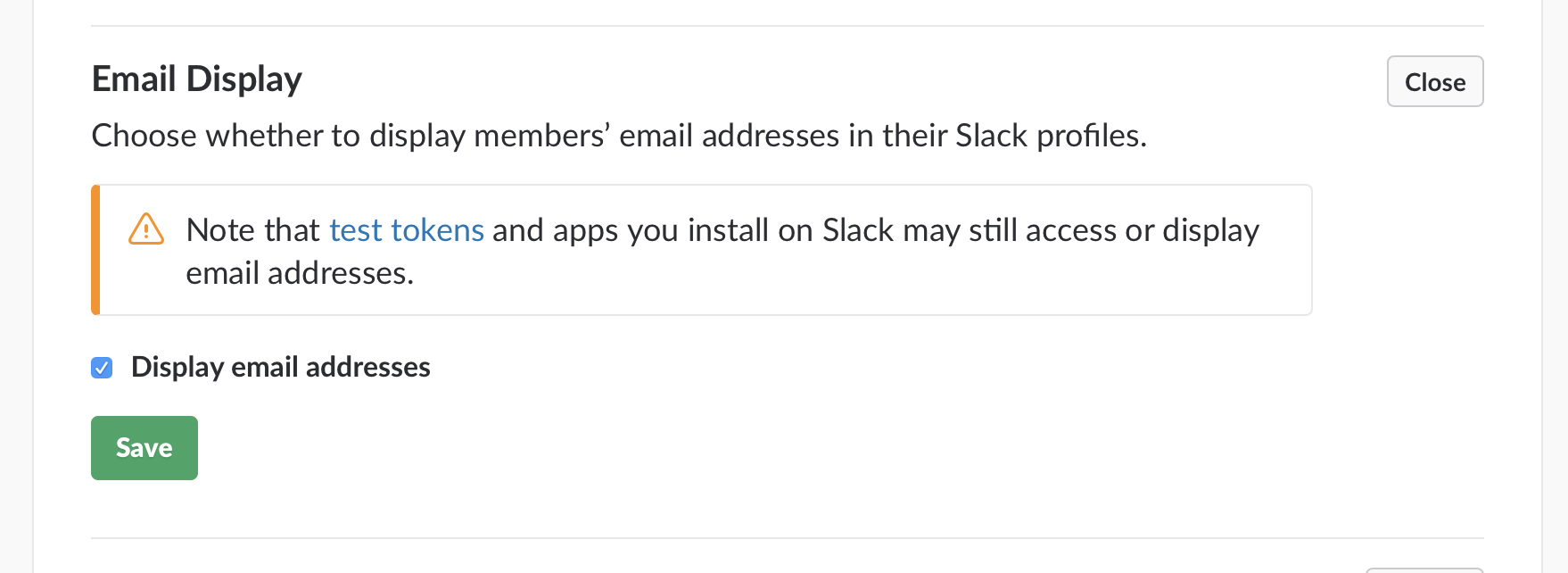
You can chose to make email addresses public. This requires each person to know which email address the person they think they're talking to used to register. It means you also have to get in the habit of clicking the view profile link and checking to make sure the person you think you're chatting with has the right email. This is done regularly by no one ever.
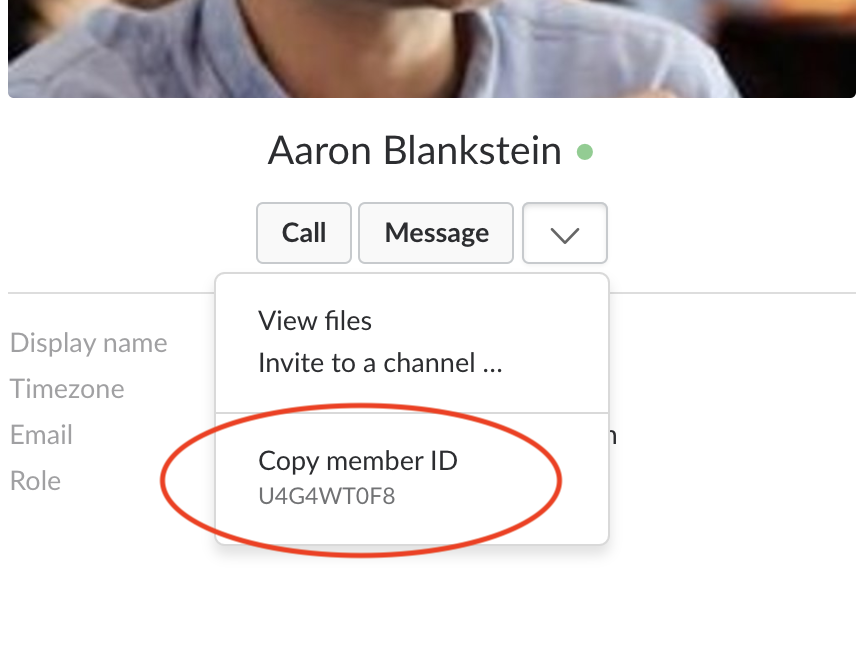
The only other sure-fire way to tell Slack users apart is by checking their Member ID. This is a 9 character, random, impossible-to-memorize-unless-you're-super-human, alphanumeric sequence hidden deep in layers of menus. Slack never tells users about it and won't let you view it on mobile devices. Useless.
Slack during a token sale
We noticed this Slack security problem in the Blockstack Slack in the run up to our token sale last fall. When we discovered it, the Blockstack core team spent a few minutes playing around with our Slack profile settings and impersonating each other.
As we prepared to handle crypto and fiat assets in our upcoming token sale, this new Slack "enhancement" created a huge new security risk. It isn't that hard to imagine how a bad actor in our 5000+ person Slack could do some serious damage. For example, the bad actor might impersonate Blockstack co-founders Ryan or Muneeb in Slack direct messages and pretend to offer preferential access to the token sale in exchange for Bitcoin transfers to an address controlled by the imposter.
Another nightmare scenario was a bad actor impersonating a trusted Blockstack team member and taking advantage of that trust to obtain valuable credentials or permissions from a colleague.
Our response
Bad people like to impersonate good projects during token sales because they see it as an easy way take advantage of trusting investors and make a quick buck.
At Blockstack, we took a number of operational steps to remove Slack from the trusted role it had had in organizing our team and coordinating our community:
- We disabled automatic registration for new users and asked users who wanted to join the Slack to go through an application process and manual review.
- We announced to our community that the they should not trust messages from anyone on Slack.
- We instituted a process where sensitive requests are verified out-of-band through a alternate secure channel.
We lucked out in that the mitigation steps we took worked and our nightmare Slack scenarios didn't occur. This freed up our time to deal with bad actors elsewhere on the internet.
Reaching out to Slack
We reached out to Slack's CEO, Stewart Butterfield, to make sure he was aware of the problem:
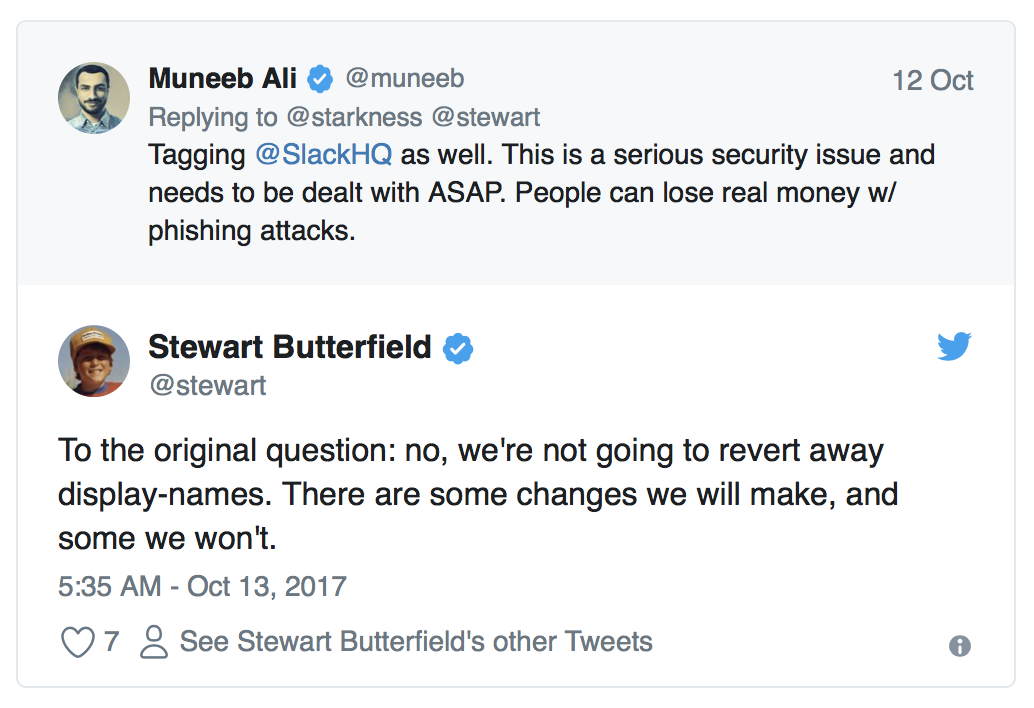
Stewart seems to be more focused on Slack’s ability to be a developer platform than it’s role as a trusted communications tool where teams can be sure that the team member they’re interacting with is who she claims to be.
Even if Slack cared deeply about this problem, no single person or company should have this much control over trust and identity online.
Our Blockstack chat bounties

At the end of 2017, we launched the $50,000 Signature Bounty to Decentralize Communication through the Blockstack Signature Fund. This competition is for two decentralized chat tools, a peer-to-peer encrypted chat and a community messaging Slack replacement. These apps will be built on Blockstack so that users, not platform CEOs, own their own identity and control their own reputations.
Don't trust middlemen
We, along with many other organizations and communities, invited Slack into our professional lives, offices and communities, and trusted them with some of our most valuable relationships.
Slack violated that trust when they changed their platform to make it so that anyone can impersonate anyone else. More importantly, Slack showed us how trusted third parties can quickly turn in to security holes for your organization and represent real business risk for your company.
Want to join us in building a world where you can use apps without trusting third parties? We're hiring!
Thanks to Muneeb Ali, Aaron Blankstein, Xan Ditoff, Sebastian Dunkel, Yukan Liao, Jude Nelson, and Jack Zampolin and everyone else that provided feedback on drafts of this post.
